Infiltrator
4.60
Size: 1.18 MB
Downloads: 6107
Platform: Windows (All Versions)
A network can have any number of vulnerabilities and it can be very difficult to spot them. With the standard Windows tools, we can barely resolve a simple connection issue, so when it comes to security, we should turn to third party software. If you urgently need to find security holes in your network or other problems, Infiltrator is just what you need. It will scan your Local Area Network and audit any connected computers for various information, regarding the safety of your network.
There are no network related settings to make while going through the setup process. It is straightforward and fast and you can run the program on most Windows versions. The package is 1.18 Mb large, so it can be downloaded in a few seconds, regardless if you have a fast or slow Internet connection.
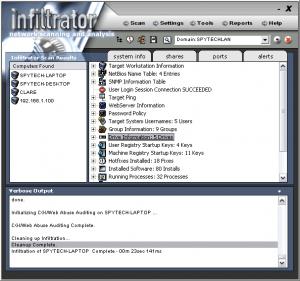
To start scanning a computer from your network, you need to type its name or IP address in a small dialog box on the toolbar and click the Scan option next to it. A context menu will pop up and you can choose certain actions like starting or stopping the scan, performing a scan with your current credentials, with a NULL session or with your login information.
The progress of the scan is displayed on the lower part of the interface and when it is done, the results will be displayed in a tree menu, on the main region of the window. You will find basic information about the target workstations, web server information, password policies, installed hotfixes, software, running services and processes and much more.
Other sets of results, such as open ports or file shares, can be accessed with the options on the left part of the interface. The software will also perform a security audit and analysis and it will display the results the same way. If there are any problems, the related components, from the tree menu, will have a different icon. Reports can be configured and generated by clicking the Reports button on the toolbar and choosing one of the options which will show up in a context menu.
It is also possible to start scanning one or more networked computers with the aid of a wizard. It can be launched from the Scan button's context menu or with one of the options on the left side of the interface. After launching the wizard, you will find multiple scanning options. You can choose to scan a specific computer, by typing its name, scan more computers, using a range of IP addresses or scan an entire network domain. During the next step of the wizard, you can opt for a complete scan, an HTTP, port or a simple scan. When you are done with the wizard, the software will perform the scan according to your specifications, and it will display the results the same way.
A series of network security tools can be activated with the options on the left side of the window. They include a WhoIs lookup tool, a raw HTML viewer, a port scanner, ping sweeper and more.
Pros
Infiltrator can be installed rapidly and it is very easy to understand. It comes with a large number of scanning options and other features, which will help you analyze every aspect of your network and the computers which are connected to it.
Cons
You can only scan your own computer with the trial version. Infiltrator will provide you with all the information you need in order to keep your network secure. Any option on its interface can be used without any effort.
Infiltrator
4.60
Download
Infiltrator Awards

Infiltrator Editor’s Review Rating
Infiltrator has been reviewed by Frederick Barton on 11 May 2012. Based on the user interface, features and complexity, Findmysoft has rated Infiltrator 5 out of 5 stars, naming it Essential